NAS Architecture⚡How NAS Works Under the Hood


NAS Architecture Explained; How NAS Works Behind the Scenes A practical, end to end guide, data path, protocols, caching, filesystems, RAID geometry, and network concurrency The Mental Model: Three Planes, One System A clean way to think about nas architecture is as three planes that share the same hardware: Protocol plane: SMB, NFS, or iSCSI […]
What Is NAS Storage?


What Is NAS Storage and Why It Matters for Modern Businesses In this article, we’ll answer one of the most common business technology questions: what is NAS storage and how does it work for organizations of any size? what is NAS (Network Attached Storage) ? Network Attached Storage (NAS) is a hardware device connected to […]
NAS vs Cloud Storage, Which Is Better for Your Business?


NAS vs Cloud Storage: Exploring the Core Concepts What Is NAS (Network Attached Storage)? NAS, or Network Attached Storage, is a physical storage device connected to your local network. It provides centralized access to files for authorized users across multiple devices, computers, workstations, servers, or mobile phones, within the same network or through secure remote […]
Cloud storage


Cloud Storage Explained: From OneDrive to Your Own Private Cloud What Is Cloud Storage? Cloud storage refers to a model of data storage where digital information is kept on remote servers accessed through the internet. These servers are maintained and operated by hosting providers who manage data availability, security, and backup. In simpler terms, rather […]
Future of Ransomware


Threat Economics: How Profit Models Will Drive the Future of Ransomware The Future of Ransomware is fundamentally economic. Attackers optimize for return on investment: lower development cost, higher victim yield, and faster monetization. The ransomware as a service model commoditized access to destructive payloads and created affiliate markets. Expect further specialization in this economy: affiliate […]
Legal & Ethical Aspects of Ransomware


Legal & Ethical Aspects of Ransomware: Navigating the Gray Areas of Cyber Extortion The Legal Landscape: When Cybercrime Meets Law Ransomware is not just a cybersecurity issue, it’s an evolving area of law that exposes the core Legal & Ethical Aspects organizations must navigate when responding to cybercrime. Governments worldwide have developed frameworks to regulate […]
Famous Ransomware Attacks


How Ransomware Really Spreads (and Why It Still Works) Despite years of awareness campaigns, ransomware remains effective because it exploits what never changes, human error, misconfigured systems, and unpatched vulnerabilities. Most attacks begin with phishing emails or stolen credentials and expand through lateral movement in flat networks. If you want a full breakdown of these […]
Ransomware Recovery Solutions


How to Restore Systems and Data Without Paying the Price The Real Work Begins After Containment Even after you stop a ransomware attack and contain its spread, the hardest and most critical phase still lies ahead: recovery. Ransomware Recovery Solutions are the bridge between chaos and control the structured approach that helps your organization rebuild […]
Ransomware Detection & Response


Ransomware Detection & Response: How to Identify, Contain, and Recover Fast What Is Ransomware Detection & Response Ransomware Detection & Response is the discipline of identifying ransomware activity as early as possible and executing predefined actions to contain, eradicate, and recover from the attack. It bridges the gap between prevention and recovery by turning weak […]
6 Ransomware Prevention Strategies


Layered Approach to True Cyber Resilience Modern organizations can’t rely on a single defense line to stop ransomware. Effective Ransomware Prevention Strategies require a multi layered framework, one that integrates prevention, detection, and recovery into a unified security posture. Each layer strengthens the other, building long-term resilience against advanced ransomware threats. 🧱 Layer 1: Prevention, […]
How Ransomware Attacks Work: Stages,Examples,Strategies


How Ransomware Attacks Work: Stages, Examples, and Defense Strategies Why Understanding How Ransomware Attacks Work Matters Ransomware has become one of the most disruptive and costly forms of cybercrime worldwide. Understanding how ransomware attacks work is essential for any organization that relies on digital operations. A ransomware attack directly impacts business continuity by locking or […]
Types of Ransomware


How Zero Trust Ransomware Defense and Hardware Firewalls Stop Modern Threats What is Ransomware? At its core, ransomware is malicious software designed to block access to data or systems until a ransom is paid. In most cases, attackers use phishing emails, malicious attachments, compromised credentials, or vulnerabilities in unpatched systems to gain entry. Once inside, […]
Zero Trust MFA; Expert Playbook


Zero Trust MFA: a clear, working guide that teams actually use Phishing-Resistant MFA (FIDO2/WebAuthn) for Admins Privileged paths control policy and production data. For these routes, Zero Trust MFA should default to phishing-resistant authenticators like FIDO2/WebAuthn. Origin-bound cryptography stops real time phishing proxies and removes most AiTM tricks. Issue at least two keys per admin […]
Endpoint Security
Endpoint Security Examples and the Complete Awareness Stage Guide What Is Endpoint Security, Really? An endpoint is any device that connects to your network: laptops, desktops, smartphones, tablets, servers, and IoT equipment. Endpoint security is the coordinated set of agent software, cloud consoles, rules, and analytics that prevent, detect, and respond to threats on those […]
What is IAM (Identity & Access Management)?


The Evolution of IAM Early IAM centered on directories and on-prem appsLDAP, Kerberos, and Microsoft Active Directory. As organizations adopted SaaS and mobile, IAM (Identity & Access Management) expanded to federation and centralized cloud brokers. Today, identity sits at the core of Zero Trust, bringing continuous verification and risk adaptive policies. On prem era: Password […]
Micro-segmentation Zero Trust
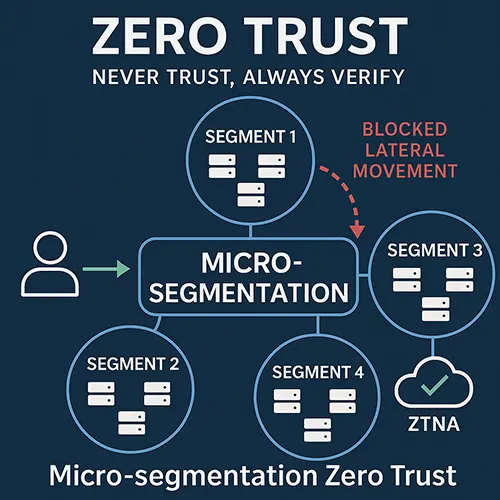

Why Micro-segmentation Zero Trust Matters Cyber attackers no longer rely solely on breaking through the network perimeter. Once inside, they move laterally across systems, escalating privileges and exfiltrating data. Traditional defenses often fail to contain this spread. This is where micro-segmentation in Zero Trust model comes in.By breaking the network into small, identity based segments, […]
SIEM & Analytics in the Zero Trust Era: A Complete Guide for 2025


Why Everyone is Searching for SIEM & Analytics Cybersecurity is evolving at lightning speed. Threats are no longer limited to perimeter attacks; they move laterally, exploit identities, and often hide in plain sight.This is why SIEM & Analytics (Security Information and Event Management with advanced analytics) has become one of the hottest search terms among […]
SIEM Integration Strategies


SIEM Integration Strategies: How to Make Security Operations Actually Work Why SIEM Integration Can’t Be an Afterthought When a SIEM is properly integrated, it doesn’t just centralize logs; it connects the dots. It helps teams: See threats clearly across endpoints, servers, cloud, and networks. Cut through the noise by filtering repetitive or low value data. […]
Zero Trust Model Explained


Complete Guide to the Zero Trust Model What is the Zero Trust Model? At its core, Zero Trust model is a security framework based on “never trust, always verify.” It eliminates implicit trust and enforces strict verification before granting access. Key principles of the Zero Trust architecture include: Continuous authentication and authorization of users and […]
Password Security Best Practices


Why Password Security Still Matters in 2025 Some argue that passwords are becoming obsolete. While it’s true that passwordless technologies such as FIDO and passkeys are gaining momentum, the reality is that passwords are still the backbone of authentication. Banking systems, enterprise networks, VPNs, and countless web platforms continue to rely on them. For organizations […]
Network Hardening Checklist


Ultimate Network Hardening Checklist: Step by Step Guide to Securing Your IT Infrastructure What is Network Hardening and Why Does It Matter? Network hardening is the process of securing your IT infrastructure by reducing vulnerabilities, enforcing strong policies, and layering defenses. A well structured Network Hardening Checklist helps organizations follow these steps in a systematic […]
Top 7 Firewall Misconfigurations

Top 7 Firewall Misconfigurations 1. Weak or Default Passwords It’s almost embarrassing that this problem still exists in 2025, but weak passwords remain one of the biggest firewall misconfigurations. Many organizations deploy firewalls products quickly, leaving the default admin credentials in place. Hackers know this and run automated scans across the internet looking for devices […]
AI-Powered Firewalls👍The Future of Network Defense


What Makes a Firewall “AI-Powered”? An AI-powered firewall is essentially an NGFW integrated with AI/ML capabilities, enabling it to adaptively inspect, learn from, and respond to threats beyond static rule-based systems. Key Features: Threat Prevention via Anomaly Detection: Capable of identifying both known and zero-day attacks by learning normal network behavior and flagging anomalies. Inline […]
How to Protect Your Organization from Ransomware attacks


The Complete Guide to Protecting Against Ransomware Attacks in 2025 In 2025, ransomware has evolved beyond simple file encryption, it’s now part of a global cybercrime economy involving data exfiltration, double extortion, and AI-driven attacks. The financial and reputational impact on organizations has made ransomware one of the top cybersecurity concerns worldwide. What is a […]
Best Practices for Optimizing FortiSIEM


Why FortiSIEM Optimize Matters The effectiveness of any SIEM depends on three core factors: speed, stability, and scalability. FortiSIEM provides rich functionality [from unified log ingestion to compliance dashboards] but poor optimization can lead to slow queries, unnecessary alerts, and even system outages. A consistent FortiSIEM Optimize strategy ensures that the platform delivers: Faster incident […]
FortiSIEM vs Other SIEM: Ultimate Secure Solution


FortiSIEM vs Other SIEM Solutions: The Ultimate Comparison for Secure Cybersecurity in 2025 Why Compare FortiSIEM vs Other SIEM Solutions? The 2025 cybersecurity landscape demands proactive solutions to counter ransomware, insider threats, and zero-day exploits. SIEM solutions are the backbone of security operations centers (SOCs), offering centralized monitoring, real-time threat detection, and compliance management. FortiSIEM […]
FortiSIEM Features


FortiSIEM Features: Comprehensive Guide to Advanced Cybersecurity Solutions in 2025 Why FortiSIEM Matters for Your Organization in 2025 The cybersecurity threat landscape in 2025 is marked by an alarming increase in ransomware attacks, supply chain vulnerabilities, and zero day exploits. According to recent industry reports, cyber incidents have risen by over 20% year over year, […]
FortiSIEM 7.4 SOAR Automation


FortiSIEM 7.4 SOAR Automation: Redefining Security Operations with GenAI Why SOCs Need FortiSIEM 7.4 SOAR Automation SOCs today face unprecedented challenges, primarily due to alert fatigue. Analysts often sift through thousands of alerts daily, many of which are false positives or low priority, making it difficult to focus on real threats. This overload can lead […]
FortiSIEM: Your Complete Security Event Management Solution


What is FortiSIEM? Next generation SIEM platform that integrates security, performance monitoring, and compliance management into one unified system. Unlike traditional SIEM tools that focus solely on security logs, combines network operations and security operations for a holistic view of your environment. FortiSIEM Product Overview | Product Demo Key Advantages Over Legacy […]
Fortinet Monitoring: Enhanced Security & Network Oversight


Fortinet Monitoring: Comprehensive Network Oversight for Enhanced Security and Performance What is Fortinet Monitoring? Fortinet Monitoring involves a set of tools and processes designed to oversee the health, performance, and security of networks using Fortinet products. At its core, Fortinet Monitoring provides real-time tracking of network metrics, such as traffic patterns, device status, and potential […]
IAM for Medium Businesses: Must-Haves and Best Practices


IAM for Medium Businesses: Why Identity & Access Management Matters Why It Matters for Medium Sized Organizations Refers to a set of policies, processes, and technologies that manage digital identities and control access to an organization’s resources. It ensures that the right users have the right access to the right resources at the right time. […]
FortiAI: The Next Evolution in Enterprise Security


Key Cybersecurity Challenges Solved by FortiAI Modern businesses face a complex threat landscape that traditional security tools struggle to counter. FortiAI directly addresses these issues with its advanced AI capabilities: AI-Powered Threats: Cybercriminals now use AI to create polymorphic malware and adversarial attacks that evade static defenses. FortiAI’s machine learning models detect these emerging threats […]
Fortigate Traffic Logs


How Fortigate Traffic Logs Work Fortigate Traffic Logs are generated by Fortigate firewalls to monitor the flow of network traffic. These logs capture detailed data about all network connections that are allowed or blocked by the firewall. Fortigate traffic logs are created in real time as traffic passes through the firewall, recording key information for […]
Complete Guide to Fortinet Firewall Logging: Best Practices & Setup


What Is Fortinet Firewall Logging? Fortinet firewall logging refers to the process of recording data on the activities occurring in your network through Fortinet’s firewalls. These logs provide detailed information about firewall activity, including data on allowed and blocked connections, network traffic patterns, intrusion attempts, and even administrative changes. By capturing detailed logs, network administrators […]
UTM vs NGFW for SMBs


What Are UTM and NGFW? What is UTM? Unified Threat Management (UTM) combines several essential security features into a single device. It includes a firewall, antivirus, VPN, web filtering, and more. For many SMBs, UTM vs NGFW often boils down to ease of use and cost. UTMs are ideal for smaller networks, where simplicity and […]
Fortinet Data Center Firewall Features


What is Fortinet Data Center Firewall? A Fortinet Data Center Firewall is a network security solution designed to protect data centers from a wide range of cyber threats. These firewalls go beyond traditional security mechanisms by integrating advanced technologies that offer deep visibility and protection against sophisticated attacks. Built on FortiGate’s next-generation firewall (NGFW) architecture, […]
Why Fortinet SD-WAN is the Smart Choice for Modern Enterprises?


What is SD-WAN and Why It Matters SD-WAN is a revolutionary networking approach that separates the control plane from the data plane, enabling centralized control and intelligent traffic routing across multiple WAN connections (such as broadband, LTE, and MPLS). It allows businesses to route traffic based on business intent, optimize application performance, and lower operational […]
Best Fortinet Firewall for Enterprise


Why Choose Fortinet for Enterprise Security? Fortinet is widely recognized as one of the most trusted names in cybersecurity. Their products are specifically designed to address the complex needs of enterprise networks. From small businesses to large multinational organizations, Fortinet firewalls provide powerful, scalable, and high-performance security solutions. Fortinet’s Reputation Among Enterprises The best Fortinet […]
Ultimate Solution Fortinet Small Business Firewall


Why Small Businesses Need a Reliable Firewall Solution Small businesses, while essential to the economy, are particularly vulnerable to cyberattacks. With limited budgets for advanced security solutions, these businesses need affordable yet effective protection against a wide range of threats, including ransomware, phishing attacks, and data breaches. Without a proper security solution, a cyberattack can […]
Evolution AI-Driven Adaptive Firewalls


What Are Next-Generation Firewalls (NGFW)? Before diving into the world of AI-Driven Adaptive Firewalls, it’s essential to understand Next-Generation Firewalls (NGFWs). These advanced firewalls address the limitations of traditional firewalls by integrating multiple security functions, including Deep Packet Inspection (DPI), Intrusion Prevention Systems (IPS), and Application Control. These capabilities allow NGFWs to identify and block […]
Best open source firewall


Best Open Source Firewall Solutions: A Complete Guide What Is an Open Source Firewall? An open source firewall is a network security system available to the public for use, modification, and distribution. Unlike proprietary firewalls, open-source firewalls are transparent in design, allowing administrators to customize rules and configurations down to the source code level. These […]
How Does Fortinet Work? Guide to Fortinet’s Security


How Does Fortinet Work? A Complete Guide to Fortinet’s Security Platform What Is Fortinet? Fortinet is a cybersecurity company. It doesn’t offer one product. It offers many. These tools include firewalls, endpoint security, Wi-Fi, SD-WAN, email filtering, and more. What makes Fortinet different is how these tools connect. They work under what’s called the Fortinet […]
Fortinet vs Imperva: Technical Comparison


Fortinet vs Imperva: A Deep Technical Comparison Without the Buzzwords ✅What Each Platform Is Built For in Fortinet vs Imperva Fortinet is fundamentally a network security platform. Its flagship product, FortiGate, is a next-generation firewall (NGFW) built to secure network traffic across data centers, branches, and edge environments. Fortinet’s strength lies in its ability to […]
Top Fortinet Security Features


Top Fortinet Security Features Uncovered: Why It’s a Leader in Cyber Defense Introduction to Fortinet Security Fortinet is a global leader in broad, integrated, and automated cybersecurity solutions. Founded in 2000, Fortinet has grown to protect hundreds of thousands of enterprises, service providers, and government organizations. Its mission is to deliver top-tier security across the […]
Why UTM Unified Threat Management Matters?


UTM Unified Threat Management: Comprehensive Guide A businesses face an ever growing array of cyber threats from sophisticated malware and phishing attacks to data breaches and insider threats. Managing these risks with traditional, standalone security tools is not only complex but also inefficient and costly. This is where utm unified threat management (UTM) comes in. […]
Fortinet Cloud security


Fortinet Cloud: Securing Hybrid Infrastructures with Advanced Cloud Security Solutions Understanding Fortinet Cloud Security What is Fortinet Cloud? Fortinet Cloud refers to a range of security solutions designed by Fortinet to protect applications, workloads, and data across various cloud environments, including public, private, and hybrid infrastructures. The key feature of these solutions is their ability […]
Benefits of Layer 7 Firewalls
Layer 7 Firewall: The Ultimate Solution for Advanced Application Security What is a Layer 7 Firewall? A Layer 7 firewall operates at the Application Layer of the OSI (Open Systems Interconnection) model, which is the top layer responsible for managing communication between software applications. Unlike traditional firewalls, which operate at lower layers (network and transport), […]
FortiSIEM vs FortiAnalyzer
FortiSIEM vs FortiAnalyzer: Choosing the Right Fortinet Security Solution for Your Needs Understanding the Core Functionality When choosing between FortiSIEM and FortiAnalyzer, decision makers often face confusion. While both tools enhance security visibility and threat intelligence, they serve very different purposes in a cybersecurity strategy. In this comprehensive comparison, we’ll break down features, deployment use […]
Top Benefits of Firewall as a Service (FWaaS)


Top Benefits of Firewall as a Service for Remote Teams in 2025 Why FWaaS is a Game Changer for Remote Work What is Firewall as a Service ? Firewall as a Service is a cloud-based firewall solution that delivers centralized security without physical hardware. It allows companies to enforce security policies across devices and users, […]
Best NAS Storage for 4K Video Editing Teams


NAS for Video Editing What is NAS? Network Attached Storage (NAS) is a storage solution that connects to a network, allowing multiple users to access and store data centrally. Unlike traditional external hard drives or direct attached storage (DAS), NAS provides shared storage, which can be accessed over a local area network (LAN) or the […]
Fortinet for Home


Why Fortinet for Home Networks? The digital transformation of our homes has brought a surge in connected devices-from smart TVs and gaming consoles to security cameras and IoT appliances. With this connectivity comes a heightened risk of cyber threats that traditional consumer routers struggle to address. As a result, more homeowners are turning to enterprise […]
Sophos Central


Sophos Central: Features You Need to Know What is Sophos Central? Sophos Central is a cloud-native cybersecurity platform designed to centralize the management of Sophos’ next-generation security solutions. Unlike traditional security tools that require multiple dashboards and complex configurations, Sophos Central brings everything together in a single, user-friendly interface. It supports a wide range of […]
AI Network Security


How AI is Transforming Network Security in Modern Enterprises The Role of AI in Network Security: A Paradigm Shift AI Network Security is playing a critical role in revolutionizing how enterprises approach cybersecurity. Traditional network security methods, such as firewalls and antivirus programs, are increasingly being replaced by more dynamic, AI-driven solutions. By utilizing machine […]
How to Detect Insider Threats?


Understanding and Detecting Insider Threats What is an Insider Threat? An insider threat refers to any risk posed by individuals within an organization who have access to its systems or data. This includes current or former employees, contractors, or business partners who might misuse access—intentionally or accidentally—to harm the business. Types of Insider Threats in […]
Barracuda Network Security vs Fortinet vs Sophos


Barracuda vs Fortinet vs Sophos: Which Network Security Solution is Right for You? Why Network Security Matters? With cyber threats evolving daily, organizations of all sizes need a comprehensive and proactive defense strategy. A robust network security solution not only protects against malware, ransomware, and phishing but also ensures business continuity, data integrity, and regulatory […]
Best Web Filtering Tools for Businesses


What is web filtering, and which tools are best for my business, especially for small businesses? What is Web Filtering? Web filtering involves monitoring and controlling internet traffic to restrict access to specific websites, content, or applications based on predefined policies. By implementing web filtering, businesses can: Enhance Security: Block malicious websites and prevent malware […]
Fortinet vs Palo Alto: Deep Dive


Fortinet vs Palo Alto: Brand Overview Fortinet Founded in 2000, Fortinet quickly became a powerhouse in network security with its FortiGate firewalls. Known for its hardware-accelerated firewalls, integrated security fabric, and cost-effective solutions, Fortinet serves businesses of all sizes. 👉 Discover our full range of Fortinet products. Palo Alto Networks Palo Alto Networks, established in […]
Synology Hybrid RAID


Synology Hybrid RAID (SHR): A Comprehensive Guide to Unlocking Its Power Unpacking SHR: The Inner Workings of Synology’s Hybrid RAID Technology Synology Hybrid RAID (SHR) is best defined as Synology’s proprietary, automated RAID management system, exclusively developed for their Network Attached Storage (NAS) product line. Its primary design goal is to simplify the deployment of […]
SASE Security


What is SASE Security? SASE (Secure Access Service Edge) is a security framework introduced by Gartner in 2019. It combines wide-area networking (WAN) capabilities with comprehensive security services like: Secure Web Gateway (SWG) Cloud Access Security Broker (CASB) Firewall as a Service (FWaaS) Zero Trust Network Access (ZTNA) Software-Defined WAN (SD-WAN) All delivered through a […]
Zero Trust Network Access (ZTNA)


How Zero Trust Network Access (ZTNA) Changes Traditional Security What is Zero Trust Network Access (ZTNA)? Let’s start with the basics. Zero Trust Network Access (ZTNA) is a security framework built on a simple but radical idea: trust no one by default. Whether you’re an employee logging in from the office or a contractor accessing […]
Guide to WAF Fortinet Models & Price


WAF Fortinet: A Complete Guide to FortiWeb for Website Security What Is WAF Fortinet? A Web Application Firewall (WAF) is a security tool designed to protect web applications by filtering and monitoring HTTP traffic between the application and the internet. WAF Fortinet, known as FortiWeb, is Fortinet’s specialized WAF solution that combines advanced security features […]
Sophos XGS 3100 vs XGS 3300


Sophos XGS 3100 vs XGS 3300: A Comprehensive Comparison to Guide Your Firewall Purchase Choosing the right firewall is a critical decision for businesses of all sizes. Sophos, a globally recognized leader in cybersecurity, offers a range of next-generation firewalls (NGFWs) designed to meet diverse organizational needs. Among their popular mid-range offerings are the Sophos […]
Comparing Sophos XGS Firewalls


Comprehensive Guide to Comparing Sophos XGS Firewalls The Sophos XGS series represents a significant advancement in firewall technology, offering enhanced performance, robust security features, and seamless integration capabilities. Understanding the distinctions between these models is crucial for organizations aiming to align their security infrastructure with specific operational needs. Why Sophos XGS Firewalls? The Sophos XGS […]
Firewall Configuration Best Practices for Organizational IT Teams


Why Firewall Configuration Matters Firewalls act as gatekeepers, filtering traffic between trusted internal networks and potentially hostile external environments. According to a 2023 report by Cybersecurity Ventures, cybercrime costs are expected to reach $10.5 trillion annually by 2025, with misconfigured security tools contributing to over 30% of breaches. A poorly configured firewall can leave gaping […]
FortiGate 120G vs FortiGate 200F


Fortinet FortiGate 120G vs FortiGate 200F: Which Firewall Fits Your Network? Overview of FortiGate 120G and FortiGate 200F Before diving into the specifics, let’s brief overview of each model. What’s the FortiGate 120G? The FortiGate 120G is part of Fortinet’s newer “G-series” lineup, introduced in 2023. It’s a compact, high-performance NGFW powered by Fortinet’s fifth-generation […]
FortiGate vs FortiWeb | Which Security Solution is Right for You?


FortiGate vs FortiWeb: Why Your Choice Matters? Cyber threats are evolving at an alarming pace, and organizations must proactively address vulnerabilities to protect their critical assets. Selecting the right security tools plays a vital role in safeguarding networks, applications, and sensitive data. FortiGate and FortiWeb are designed to mitigate different types of risks, making it […]
Fortinet Acquires Perception Point


How Fortinet Acquired Perception Point: Enhancing Cybersecurity for the Modern Workspace The Strategic Acquisition: A Game-Changer for Cybersecurity Securing communication platforms has never been more critical. Fortinet’s acquisition of Perception Point signifies a substantial shift toward comprehensive and integrated cybersecurity. Perception Point is known for its advanced security solutions, particularly in email security and collaboration […]
NAS vs External Hard Drive


NAS vs External Hard Drive: Which One Should You Choose? Before comparing NAS vs External Hard Drives, let’s first clarify what each storage option is and how they function What is a NAS (Network Attached Storage)? NAS (Network Attached Storage): NAS is a dedicated storage device that connects to your network, allowing multiple devices […]
Best Cyber Security


Top Cyber Security Threats and How to Prevent Them Cyber threats evolve constantly, making it crucial for businesses to stay ahead with the best cyber security practices. Below are some of the top threats and prevention strategies. Threat Description Prevention Phishing Attacks Fake emails tricking employees into revealing sensitive information Employee training and email filtering […]
Best Security Software for Synology NAS


Why Security for Synology NAS Matters Synology NAS Security is crucial for protecting centralized storage accessible over a network, making it indispensable for businesses and individuals alike. With the rise of cyberattacks, including ransomware, phishing, and unauthorized access, securing NAS devices is no longer optional. The potential risks include: Data breaches exposing sensitive information. Loss […]
Synology Home NAS + Best synology for home use


Synology Home | synology nas for home use Network Attached Storage (NAS) is a dedicated file storage system that connects to a home or office network, providing centralized access to data across multiple devices. In recent years, Synology has emerged as one of the leading manufacturers in the NAS market, offering a wide range […]
Network Security Best Practices for the Holidays: Proactive Solutions


Key Risks and Vulnerabilities During the Holidays Phishing Scams: Holiday-themed emails offering discounts or charitable requests often disguise malicious links or attachments. Both businesses and individuals are prime targets. Following Network Security Best Practices for the Holidays can help you recognize and avoid these scams. Ransomware Attacks: Cybercriminals exploit the reduced staffing of IT teams […]
WAF vs Network Firewall
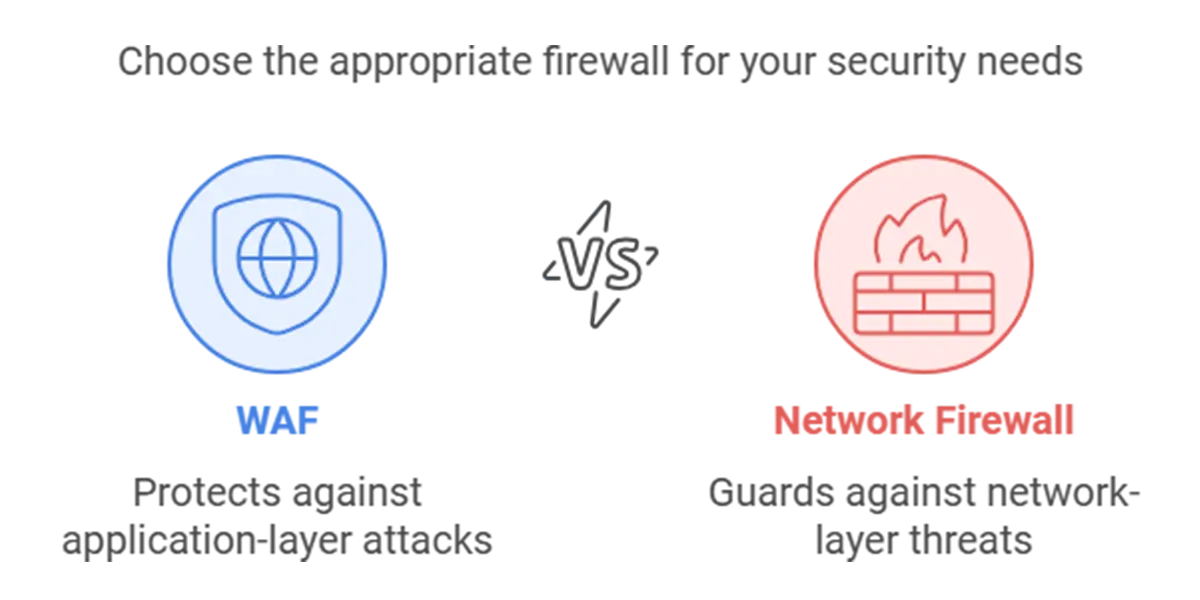

WAF vs Network Firewall: Understanding the Distinctions and Choosing the Right Security Solution In the realm of cybersecurity, understanding the distinctions between various protective measures is crucial for safeguarding digital assets. This article explores the differences between Web Application Firewalls (WAF) and Network Firewalls, highlighting their unique functionalities, use cases, and the roles they play […]
Fortinet Firewall Types


Comprehensive Guide to Fortinet Firewall Types Fortinet Firewall Types are designed to address the diverse security needs of businesses, ranging from small enterprises to large organizations. These firewalls, powered by the advanced FortiOS operating system, provide a comprehensive suite of security features, including firewall, intrusion prevention (IPS), antivirus, and web filtering, all in a unified […]
Firewall vs proxy [Difference between firewall and proxy]
![Firewall vs proxy [Difference between firewall and proxy] 117 proxy vs firewall: Digital network setup with firewall and proxy server.](https://netwisetech.ae/wp-content/uploads/proxy-vs-firewall.webp)
![Firewall vs proxy [Difference between firewall and proxy] 117 proxy vs firewall: Digital network setup with firewall and proxy server.](https://netwisetech.ae/wp-content/uploads/proxy-vs-firewall.webp)
Proxy vs firewall are two critical concepts in network security that serve distinct purposes. To effectively compare firewall vs proxy, it is essential to first understand several key concepts, such as how traffic is managed, the level of security provided, and the functionalities of each tool. Proxies act as intermediaries, facilitating requests between users and […]
Understanding the Types of Network Storage(SAN),(NAS),(DAS)


Network storage types play a critical role in modern IT infrastructure, providing organizations with scalable and efficient data management strategies. Storage Area Networks (SAN), Network Attached Storage (NAS), and Direct Attached Storage (DAS) represent distinct approaches to storing and accessing data, each with unique characteristics tailored to different operational needs. SANs offer high-speed, block-level storage […]
Synology surveillance system


Building a Robust Surveillance System with Synology: A Guide to Multi-Camera, Multi-Server Deployments Synology Surveillance is a robust network video recorder (NVR) solution developed by Synology, a renowned provider of network-attached storage (NAS) solutions. Designed to cater to the diverse security needs of modern organizations, Synology Surveillance offers a comprehensive platform for managing IP cameras […]
What is Cyber Threats?


The Evolution of Cyber Threats in the Business World Historical Overview of Cyber Threats Cyber threats have changed a lot over the years. In the past, they were mostly simple attacks like viruses that spread through floppy disks. Today, threats are much more complex and can come from many sources, including poorly secured devices. The […]
Best firewall hardware


What exactly is a firewall? When selecting the best firewall hardware, a solid understanding of firewalls is paramount. Firewalls act as security checkpoints, scrutinizing network traffic to identify and block potential threats. By implementing predefined security policies, firewalls determine which data is permitted to enter or exit a network. This mechanism is essential for safeguarding […]
Synology NAS for file sharing


Share File Links and Manage Files on Synology NAS with DSM – File Station [Synology NAS for file sharing] Synology NAS for file sharing has transformed the entire landscape of document security, management, and sharing by providing users with a more efficient way to organize their files and collaborate smoothly. It is considered a […]
Active Backup for Business


UNDERSTANDING THE IMPORTANCE OF ACTIVE BACKUP FOR BUSINESS THE ROLE OF DATA SECURITY IN MODERN BUSINESS Data security is crucial for any business. Protecting sensitive information helps maintain customer trust and ensures compliance with regulations. Here are some key points to consider: Data breaches can lead to significant financial losses. Companies may face legal consequences […]
Best Web Application Firewall (WAF)

Understanding best Web Application Firewalls What is a Web Application Firewall? A Web Application Firewall (WAF) is a special tool that protects web applications. It works like a reverse proxy firewall. It checks, filters, and blocks HTTP traffic between the internet and your web app. It does this based on specific rules. This helps keep […]
How familiar are you with Packet Filtering Firewall?


What Is a Packet Filtering Firewall? A packet filtering firewall is a type of network security tool that controls the flow of data packets entering or leaving a network. It uses a set of rules to decide whether to allow or block these packets. This process helps protect the network from unwanted access and potential […]
proxy firewalls


How Proxy Firewalls Work A proxy firewall acts as a intermediary between your internal network and the internet. It intercepts all incoming and outgoing network traffic, inspecting each packet for potential threats. By acting as a buffer between your network and the outside world, proxy firewalls can effectively protect your systems from a variety of […]
Top 10 Best NAS Storage Solutions for Secure Data Backup


Understanding the Importance of NAS Storage for Data Backup In the digital age, data has become one of the most valuable commodities, underpinning personal and professional activities alike. As our reliance on electronic files continues to grow, safeguarding this data is essential. One of the most effective solutions for backing up important information is Network […]
Differences Firewall and NGFW


Difference between firewall and next generation firewall In difference between firewall and next generation firewall, it’s essential to understand a few key concepts: Overview of Traditional Firewalls A traditional firewall is a network security device designed to monitor and control incoming and outgoing network traffic based on predefined security rules. It acts as a […]
Small business firewall

How does a firewall protect your network? A firewall is a security device that protects your network by monitoring incoming and outgoing network traffic. It examines each packet of data and blocks any that do not meet the specified security criteria, such as those associated with known malware or hackers. Small business challenges and the […]
Best Firewall: Which One is Right for You?


Why the Best Firewall is Essential for Your Online Security: A Comprehensive Guide As cyber threats go beyond every corner, the purchase of the most firewalls is a necessity rather than a precaution. A strong firewall could be said to be your first line of defense for unauthorized access and malicious attacks as it protects […]
Best Synology NAS for Backup


What is Synology NAS and Why is it Ideal for Backup? What is a NAS (Network Attached Storage)? A NAS is a special kind of device, specifically designed to facilitate the secure and centralized sharing of data via a network. The NAS devices are storage solution-specific and have a part in providing connected users with […]
Synology for Business


Synology for Business: Comprehensive Data Management and Software Solutions for Enterprises Synology for business, the organization offers data management software solutions for companies of various sizes, which involves different kinds of data management and infrastructure needs. Built on a solid and flexible architecture, Synology’s solutions come with scalable and custom-made options, thus, allowing companies […]
fortigate firewall models List


FortiGate Next-Generation Firewall models FortiGate Firewall models (Next-Generation Firewalls) provide advanced network security features for businesses of all sizes. These models offer a range of benefits, including intrusion prevention, application control, and SSL/TLS encryption. Traditional firewalls are no longer sufficient to counter the sophisticated threats that exist today, thereby necessitating the shift towards NGFWs. FortiGate, […]
20 Top FortiGate features and benefits


Core Features of FortiGate The FortiGate features have established itself as the industry standard for comprehensive network security solutions. Fortigate firewall production by Fortinet these powerful appliances offer a multitude of advanced features that empower organizations of all sizes to safeguard their networks and data from a wide range of cyber threats. At the heart […]
Fortinet Acquires Lacework

Fortinet Acquires Lacework, Bolstering Cloud Security Offerings Fortinet, a pioneer in the realm of cybersecurity innovations, boasts an impressive portfolio of patented technologies, surpassing the cumulative total of its closest competitors. This organization has garnered recognition in over 100 industry analyst reports and has been consistently featured in multiple Gartner® Magic Quadrant™ reports, a testament […]
What Is Cybersecurity? A Thorough Definition


What is cybersecurity and why is it important? Cybersecurity refers to the collection of technologies, processes, and practices designed to protect digital information, networks, and systems from unauthorized access, use, disclosure, disruption, modification, or destruction. The concept of cybersecurity has undergone significant transformation since its inception in the 1970s, when the first computer virus was […]
what is a firewall?


what is a firewall? A firewall is a security device—either hardware or software—that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on predetermined security rules. The primary purpose of a firewall is to establish a barrier between your internal network and incoming traffic from external sources (such […]
Network Security Threats UAE: Protecting Your Business in 2024


The Evolving Cybersecurity Landscape in the UAE In response Network Security Threats UAE, the government recognizes the importance of cybersecurity and has taken significant steps to address growing threats. The UAE National Cybersecurity Strategy outlines a comprehensive framework for safeguarding the nation’s critical infrastructure and promoting a secure digital environment. However, cybercriminals are constantly evolving […]
Building a Secure Business Network in Dubai


Overview of the Current Cybersecurity Landscape in Dubai Building a secure business network Dubai is crucial in today’s digital age. Dubai is a fast-growing metropolis with a thriving digital economy. This growth, however, attracts cybercriminals who exploit vulnerabilities in business networks. Statistics show a rise in cyberattacks like phishing, ransomware, and DDoS attacks. Additionally, Dubai […]
Fortifying Home Network Security: A Comprehensive Exploration of the Fortinet FortiGate Home Firewall


fortigate home use | fortigate firewall for home use | fortigate for home use As the digital landscape continues to evolve, the FortiGate firewalls stand as a trusted ally in the quest to maintain a secure and protected home environment. The FortiGate firewalls offer robust access control and user management capabilities, allowing homeowners to establish […]
10 Best-selling Fortinet FortiGate Series Firewalls in Dubai

The best-selling Fortinet FortiGate Series Firewalls in Dubai offer top-notch cybersecurity protection for businesses in the region. Fortinet FortiGate Series Firewalls have emerged as the top choice for businesses in Dubai seeking robust cybersecurity solutions. With their advanced threat protection capabilities and high-performance security features, these firewalls offer unparalleled protection against cyber threats. Businesses in […]
FortiGate VS Cisco Firewall


Overview of FortiGate When comparing FortiGate vs Cisco Firepower, it is crucial to have a foundational understanding of the historical development of both brands. FortiGate, developed by Fortinet, is a leading cybersecurity solution that offers a comprehensive range of features to protect computer networks from various threats. With a rich history and strong background in […]
What is FortiGate? [FortiGate firewall buying guide]
![What is FortiGate? [FortiGate firewall buying guide] 172 what is fortigate firewall used for](https://netwisetech.ae/wp-content/uploads/2024/04/what-is-fortigate-firewall-used-for.webp)
![What is FortiGate? [FortiGate firewall buying guide] 172 what is fortigate firewall used for](https://netwisetech.ae/wp-content/uploads/2024/04/what-is-fortigate-firewall-used-for.webp)
what is FortiGate firewall? Weaving a safe network cloth is done with proper best firewall selection. FortiGate firewalls are a security system that mainly enables checking the traffic passing through a network safely and by predetermined policies. Firewalls FortiGate are the strong and scalable security platforms produced by Fortinet. This firewall solutions have become an […]
Sophos Firewall for Small Business Buying Guide


Sophos Firewall for Small Business In today’s digital age, cybersecurity is a top priority for businesses of all sizes. Small businesses, in particular, are often targeted by cybercriminals due to their perceived vulnerability. As a result, it is crucial for small businesses to invest in robust cybersecurity solutions to protect their sensitive data and ensure […]
