How Proxy Firewalls Work
A proxy firewall acts as a intermediary between your internal network and the internet. It intercepts all incoming and outgoing network traffic, inspecting each packet for potential threats. By acting as a buffer between your network and the outside world, proxy firewalls can effectively protect your systems from a variety of cyber threats.
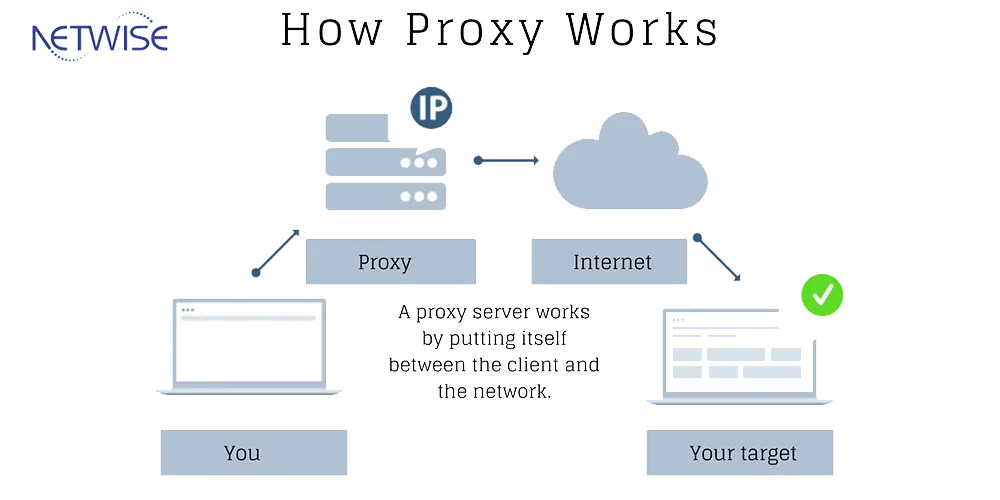
A Firewall Proxy is considered the safest type of firewall because it prevents direct contact between networks and other systems. It has its own Internet Protocol (IP) address, which means that an external network connection cannot directly receive packets from the network.
A proxy firewall functions by providing a single point that enables organizations to assess the threat level of application protocols and implement attack detection, error detection, and authentication checks. It employs tactics such as Deep Packet Inspection (DPI) and proxy-based architecture to analyze application traffic and identify advanced threats.
A proxy network typically has a computer that is directly connected to the internet. Other computers in the network access the internet through this main computer acting as a gateway, allowing the proxy to cache requested documents for multiple users.
Access process through proxy firewall
A user attempting to access an external site through the proxy firewall undergoes the following process:
- The user requests internet access via a protocol such as File Transfer Protocol (FTP) or Hypertext Transfer Protocol (HTTP).
- The user’s computer attempts to establish a session between itself and the server, sending a Synchronization (SYN) message packet from its IP address to the server’s IP address.
- The Firewalls Proxy intercepts the request and, if its policy allows, responds with a Synchronization Acknowledgment (SYN-ACK) message packet from the requested server’s IP.
- Upon receiving the SYN-ACK packet, the user’s computer sends back a final Acknowledgment (ACK) packet to the server’s IP, establishing a connection to the proxy, although it does not represent a valid Transmission Control Protocol (TCP) connection.
- The proxy then completes the connection to the external server by sending a SYN packet from its own IP address. When the server receives the SYN-ACK packet from the proxy, it responds with an ACK packet. This ensures a valid TCP connection between the proxy and the user’s computer, as well as between the proxy and the external server.
- Requests made through the client-to-proxy connection are then analyzed by the proxy-to-server connection to ensure validity and compliance with corporate policies until either party terminates the connection.
This process guarantees a highly secure network, providing deep inspection of the contents of every packet flowing in and out of the network.

Key functionalities of a proxy firewall include:
To illustrate how a proxy firewall works, imagine it as a security guard at the entrance of a building. The guard (proxy firewall) inspects everyone who wants to enter the building (network) to ensure they are authorized and pose no threat.
- Packet filtering: Examines individual packets of data to identify and block suspicious traffic.
- Application-level gateway: Controls the flow of traffic at the application layer, allowing for more granular control over network access.
- Content filtering: Scans web traffic for malicious content, such as viruses, malware, and phishing attacks.
- Caching: Stores frequently accessed web content locally to improve performance and reduce bandwidth consumption.
Benefits of Using Proxy firewall
Firewalls Proxy firewalls comprise of firewalls that act as the perfect intermediary between the end users and the external networks thus providing an additional layer of security.
The foremost advantage of using it is obviously the heightened security aspect since Firewalls Proxy serve as a conduit between clients and the outside world.
Malicious Content blocking, unauthorized access blocking, as well as protection of sensitive information are some of the security measures that proxy firewalls can achieve by filtering and thus inspecting the application data of the traffic.
Performance of proxy firewalls is further enhanced by caching frequently accessed web resources, which is yet another way to improve performance. It is a win-win situation for both users in terms of reduced load times and data transmission for more effective data transfer because of less bandwidth consumption.
Besides these, the organizations also benefit from compliance with industry regulations which would be provided by firewalls proxy that very often include strong logging and reporting features that make adherence to data protection laws and standards easier.
With this compliance, organizations can safely operate within legal frameworks while preserving a secure network environment. All in all, the adoption of proxy firewalls is a deliberate move by organizations in securing their network, optimizing performance, and complying with regulations.


Proxies for Firewalls Functionality:
Stronghold hosts provide proxy servers, which are typically used over high-probability systems subjected to direct cyberattacks. firewalls proxy inspect the communication for fundamental Internet protocols, which are including Layer 7, and should be deployed against all applications they support.
These support Domain Name System (DNS), File Transfer Protocol (FTP), Hypertext Transfer Protocol (HTTP), Internet Control Message Protocol (ICMP), and Simple Mail Transfer Protocol (SMTP) as enumerated.
firewalls proxy function as a central point of communication for all connection requests between the computers in a regular network. The proxy is the device that forms a new network link for every computer in the network to connect to the proxy.
A proxy firewall means that there is a stand-in for every communication within a network. Out of the whole network, all computers set up connections via the proxy and hence form a new link between them.
For instance, let’s assume a user wants to redirect to an external website, the packets will be channeled through an HTTP server before they reach the wanted destination.
The website’s packets are then processed through the server before being sent back to the user.
firewalls proxy centralize application activities on a single server. This allows organizations to inspect packets for more than just source and destination addresses and port numbers. As a result, most firewalls now feature some form of proxy server architecture.
Firewalls Proxy are frequently deployed within a set of trusted applications that support specific application protocols. This ensures comprehensive risk analysis for the security of the protocols and provides advanced security control compared to standard firewalls.
Firewalls Proxy : Advantages and Disadvantages
| (Advantages) | (Disadvantages) |
| Enhanced Security: | Performance Overhead: |
| By acting as an intermediary, proxy firewalls can provide a higher level of security by inspecting and filtering traffic at the application layer. | Proxy firewalls can introduce additional latency and reduce network performance, especially when handling large amounts of traffic. |
| Content Filtering: | Complexity: |
| Proxy firewalls can effectively filter content based on various criteria, such as keywords, categories, or domains. | Configuring and managing proxy firewalls can be complex, requiring specialized knowledge and expertise. |
| Improved Network Visibility: | Single Point of Failure: |
| Proxy firewalls provide detailed logs and reports about network traffic, enabling administrators to monitor and analyze network activity. | Because all traffic passes through the proxy firewall, it represents a single point of failure. If the firewall goes down, network connectivity is disrupted. |
| Caching: | Vendor Lock-in: |
| Proxy firewalls can cache frequently accessed content, reducing bandwidth consumption and improving performance. | Organizations may become dependent on a specific vendor’s proxy firewall solution, making it difficult to switch to a different product. |
| Centralized Management: | Cost: |
| Proxy firewalls allow for centralized management and policy enforcement, simplifying network administration. | Implementing and maintaining a proxy firewall can be costly, especially for large organizations. |
Choosing the Right Proxy Firewall: [Buying guide]
- Size of the network
- Security requirements
- Budget
- Scalability
When it comes to the firewall proxy choice, some crucial factors must be carefully considered in order to find the most suitable solution for the organization.
The first thing is the **size of the network** which is important. The reason why large networks require firewalls that can deal with higher traffic is that they do not affect performance. Secondly, it is necessary to know the specific **security requirements** of the organization.
These include implementing security measures that comply with regulations, protection from specific threats, and the proper integration of existing security measures.
Moreover, the **budget** is another very important aspect of decision-making. The reason is that organizations have to choose a solution that is within their financial limits yet gives the best value.
Moreover, **scalability** is another important factor that should be considered as the firewall must be able to grow along with the organization’s changing needs and thus accommodating future expansions without the need for a complete overhaul.
Differences Between Proxy Firewalls and Traditional Firewalls:
Proxy firewalls and traditional firewalls have the same main purpose of protecting the network. However, they have different operational approaches.
Unlike traditional firewalls that act as a bridge between a safe internal network and an unsafe external network, filtering traffic mainly based on IP addresses and port numbers, they allow direct connections between users and external servers, which may put the internal network at risk.
On the other hand, proxy firewalls use the delivery of requests from clients to external servers to function as intermediaries. Thus, not only conceal the inner addresses but also enables in-depth examination of the application layer traffic, which is crucial for the effectiveness of the security measures against malicious content.
proxy firewall’s top Brands:
Comparison proxy firewall solutions from leading vendors:
| Feature | Sophos | Fortinet |
| Core Functionality | Comprehensive UTM solution offering firewall, IPS, web filtering, email security, and more. | High-performance firewall with advanced threat protection, including IPS, application control, and sandboxing. |
| Performance | Known for its performance and scalability, especially in larger environments. | Offers high-performance and scalability, with a focus on hardware acceleration. |
| Threat Protection | Advanced threat protection with sandboxing, machine learning, and behavioral analysis. | Strong threat protection capabilities, including IPS, application control, and sandboxing. |
| Management | Centralized management console for easy configuration and monitoring. | Intuitive management interface with a wide range of reporting and analytics tools. |
| Cloud Integration | Seamless integration with cloud environments and IaaS platforms. | Robust cloud security capabilities, including cloud-based sandboxing and WAF. |
| Pricing | Offers flexible licensing options, including subscription-based models. | Competitive pricing with various licensing tiers to meet different needs. |
| Ease of Use | Generally considered user-friendly with a well-designed interface. | Interface can be complex for non-technical users, but offers advanced features for experienced administrators. |
| Scalability | Highly scalable to accommodate growing networks and changing security needs. | Designed for scalability, with options for both physical and virtual appliances. |
| Ecosystem | Strong ecosystem of partners and third-party integrations. | Extensive ecosystem of partners and integrations with other security solutions. |
| Key Differentiators | Sophos is known for its ease of use and strong focus on threat detection and response. | Fortinet is known for its high performance and comprehensive security features. |
Top Proxy Firewall Solutions Partner and Distributor
Netwisetech is the most favorite firewall solutions supplier and distributor in Dubai, UAE. we supplies not only high-tech hardware form Cyber Security solutions and Network security solutions so but also necessary expert help and services tailored for local businesses.
By focusing on competitive pricing, Netwisetech ensures that organizations can access the best quality firewall solutions without going over the limit of their budgets. It sets the company apart from the rest, the local expertise means that the clients know the regional security challenges and compliance requirements.
Furthermore, Netwisetech’s basic support includes consultations, firewall installation and configuration, and updates that have been made available to clients to make sure they can easily manage their network security.
The local clients can trust that when they partner with Netwisetech they will receive the best value and expertise in proxy firewall solutions.
How Netwisetech Can Help You!
Netwisetech serves as a trusted Sophos partner in UAE and a reliable Dubai Fortinet distributor broader region. By providing high-quality products from reputable brands, Netwisetech ensures that organizations, regardless of their size, can enhance their security posture effectively.
With a commitment to fast shipping worldwide, Netwisetech facilitates quick access to essential security solutions that help integrate and strengthen the security infrastructure of businesses.
Whether a small startup or a large enterprise, organizations can count on Netwisetech to deliver the tools they need to protect their assets and maintain a secure environment.





