

How to Backup to NAS: A Comprehensive Guide for Secure Data Protection Understanding NAS and


How to Backup to NAS: A Comprehensive Guide for Secure Data Protection Understanding NAS and


Fortinet Security Fabric: The Ultimate Integrated Security Solution for Modern Networks What is Fortinet Security


NAS Architecture Explained; How NAS Works Behind the Scenes A practical, end to end guide,


What Is NAS Storage and Why It Matters for Modern Businesses In this article, we’ll


NAS vs Cloud Storage: Exploring the Core Concepts What Is NAS (Network Attached Storage)? NAS,


Cloud Storage Explained: From OneDrive to Your Own Private Cloud What Is Cloud Storage? Cloud


Threat Economics: How Profit Models Will Drive the Future of Ransomware The Future of Ransomware


Legal & Ethical Aspects of Ransomware: Navigating the Gray Areas of Cyber Extortion The Legal


How Ransomware Really Spreads (and Why It Still Works) Despite years of awareness campaigns, ransomware


How to Restore Systems and Data Without Paying the Price The Real Work Begins After


Ransomware Detection & Response: How to Identify, Contain, and Recover Fast What Is Ransomware Detection


Layered Approach to True Cyber Resilience Modern organizations can’t rely on a single defense line


How Ransomware Attacks Work: Stages, Examples, and Defense Strategies Why Understanding How Ransomware Attacks Work


How Zero Trust Ransomware Defense and Hardware Firewalls Stop Modern Threats What is Ransomware? At


Zero Trust MFA: a clear, working guide that teams actually use Phishing-Resistant MFA (FIDO2/WebAuthn) for
Endpoint Security Examples and the Complete Awareness Stage Guide What Is Endpoint Security, Really? An


The Evolution of IAM Early IAM centered on directories and on-prem appsLDAP, Kerberos, and Microsoft
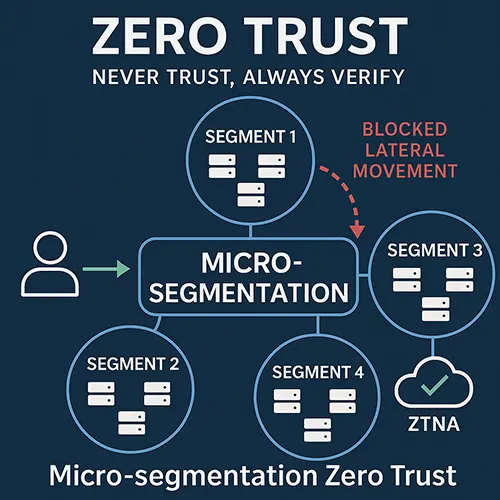

Why Micro-segmentation Zero Trust Matters Cyber attackers no longer rely solely on breaking through the


Why Everyone is Searching for SIEM & Analytics Cybersecurity is evolving at lightning speed. Threats


SIEM Integration Strategies: How to Make Security Operations Actually Work Why SIEM Integration Can’t Be


Complete Guide to the Zero Trust Model What is the Zero Trust Model? At its


Ultimate Network Hardening Checklist: Step by Step Guide to Securing Your IT Infrastructure What is


What Makes a Firewall “AI-Powered”? An AI-powered firewall is essentially an NGFW integrated with AI/ML


The Complete Guide to Protecting Against Ransomware Attacks in 2025 In 2025, ransomware has evolved


Why FortiSIEM Optimize Matters The effectiveness of any SIEM depends on three core factors: speed,


FortiSIEM 7.4 SOAR Automation: Redefining Security Operations with GenAI Why SOCs Need FortiSIEM 7.4 SOAR


Fortinet Monitoring: Comprehensive Network Oversight for Enhanced Security and Performance What is Fortinet Monitoring? Fortinet


IAM for Medium Businesses: Why Identity & Access Management Matters Why It Matters for Medium


How Fortigate Traffic Logs Work Fortigate Traffic Logs are generated by Fortigate firewalls to monitor


What Are UTM and NGFW? What is UTM? Unified Threat Management (UTM) combines several essential


What Are Next-Generation Firewalls (NGFW)? Before diving into the world of AI-Driven Adaptive Firewalls, it’s


Best Open Source Firewall Solutions: A Complete Guide What Is an Open Source Firewall? An
Layer 7 Firewall: The Ultimate Solution for Advanced Application Security What is a Layer 7


Sophos Central: Features You Need to Know What is Sophos Central? Sophos Central is a


Key Risks and Vulnerabilities During the Holidays Phishing Scams: Holiday-themed emails offering discounts or charitable


Proxy vs firewall are two critical concepts in network security that serve distinct purposes. To


The Evolution of Cyber Threats in the Business World Historical Overview of Cyber Threats Cyber


The Evolving Cybersecurity Landscape in the UAE In response Network Security Threats UAE, the government


Overview of the Current Cybersecurity Landscape in Dubai Building a secure business network Dubai is