WAF vs Network Firewall: Understanding the Distinctions and Choosing the Right Security Solution
In the realm of cybersecurity, understanding the distinctions between various protective measures is crucial for safeguarding digital assets. This article explores the differences between Web Application Firewalls (WAF) and Network Firewalls, highlighting their unique functionalities, use cases, and the roles they play in a comprehensive security strategy.

What is a Network Firewall?
A Network Firewall is a security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It serves as a barrier between a trusted internal network and untrusted external networks, such as the internet. Network Firewalls can be hardware-based, software-based, or a combination of both, and they primarily focus on filtering traffic at the network layer (Layer 3 and Layer 4 of the OSI model)
Key Features of Network Firewalls:
- Traffic Filtering: Blocks or allows traffic based on IP addresses, ports, and protocols.
- Stateful Inspection: Keeps track of the state of active connections and determines which packets to allow through the firewall.
- VPN Support: Often includes features for secure remote access through Virtual Private Networks.
- Intrusion Prevention: Some advanced firewalls incorporate intrusion detection and prevention systems (IDPS) to identify and block malicious activities.
What is a Web Application Firewall (WAF)?
A Web Application Firewall is specifically designed to protect web applications by filtering and monitoring HTTP traffic between a web application and the internet. WAFs operate at the application layer (Layer 7 of the OSI model) and are adept at identifying and mitigating threats that target web applications, such as SQL injection, cross-site scripting (XSS), and other application-layer attacks.
Key Features of WAFs:
- Application Layer Protection: Focuses on protecting web applications from specific vulnerabilities
- Custom Rules: Allows for the creation of tailored rules to address unique application security needs.
- Traffic Monitoring: Analyzes incoming and outgoing HTTP/HTTPS traffic for malicious patterns.
- Bot Mitigation: Helps in identifying and blocking malicious bots that may attempt to exploit web applications.
Key Differences: WAF vs Firewall
When it comes to protecting web applications and networks from cyber threats, two crucial security measures come into play, Web Application Firewalls (WAFs) and traditional firewalls. The concept of WAF vs Firewall is often discussed in the context of network security, with many organizations weighing the benefits of each.
In a similar vein, the comparison of WAF vs Firewall highlights the distinct approaches these security solutions take in safeguarding digital assets. A WAF is specifically designed to protect web applications from attacks such as SQL injection and cross-site scripting, while a network firewall focuses on controlling incoming and outgoing network traffic based on predetermined security rules. Understanding the role of each in the security landscape is essential for implementing an effective defense strategy.
Several key differences distinguish WAF vs Firewalls:
| Feature | Network Firewall | Web Application Firewall |
| Layer of Operation | Network Layer (Layer 3 & 4) | Application Layer (Layer 7) |
| Primary Focus | General network traffic control | Protection of web applications |
| Threat Mitigation | Blocks unwanted traffic based on IP, port, and protocol | Protects against application-specific attacks |
| Customization | Limited customization options | Highly customizable rules for specific applications |
| Use Cases | Protects entire network infrastructure | Secures individual web applications |
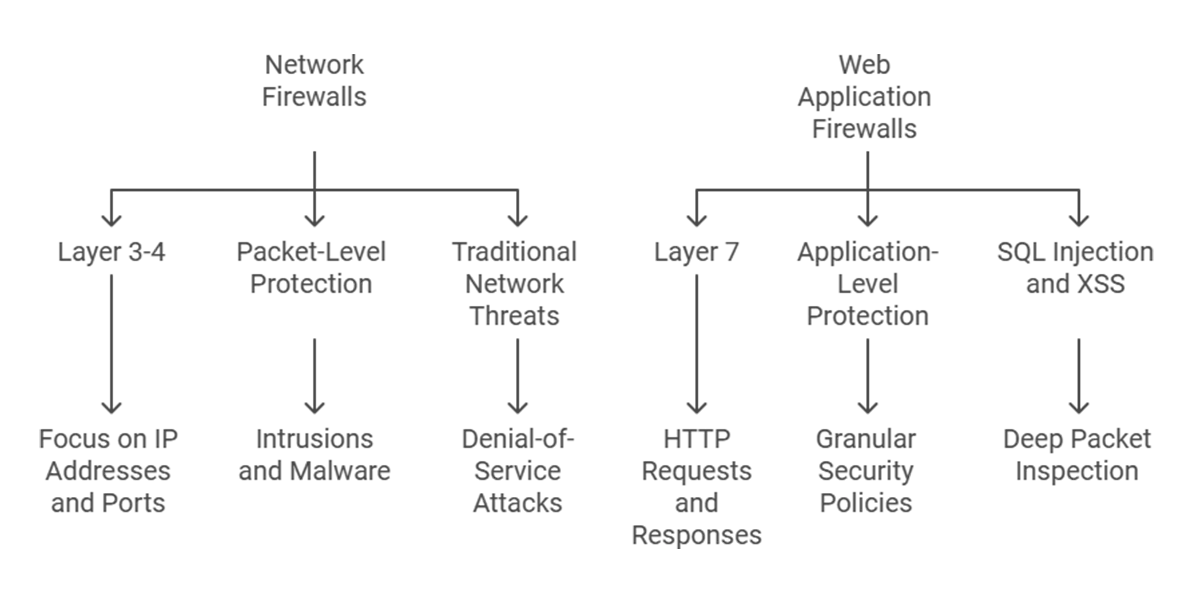
- Layer of Operation: The most fundamental difference lies in the layer at which each operates. Network Firewalls operate at the network layer (Layers 3-4 of the OSI model), focusing on packet-level information such as source and destination IP addresses and ports. WAFs, in contrast, operate at the application layer (Layer 7), examining the content of the traffic, including HTTP requests and responses.
- Type of Protection: Network Firewalls are designed to protect against traditional network threats such as intrusions, malware, and denial-of-service (DoS) attacks by controlling network access. WAFs specialize in protecting web applications from specific threats such as SQL injection, XSS, and other application-layer attacks that target web applications’ logic and input handling.
- Granularity of Control: Due to their application-layer focus, WAFs can enforce more granular security policies than Network Firewalls. For instance, a WAF can be configured to allow only specific HTTP methods (e.g., GET, POST) to certain URLs within a web application, whereas a Network Firewall’s rules would typically be based on IP addresses and ports.
- Traffic Inspection: WAFs perform deep packet inspection specifically for web traffic, allowing them to understand the context and content of HTTP communications. This enables them to detect and prevent complex web attacks. Network Firewalls, while capable of packet inspection, may not delve as deeply into the content of web traffic and are more focused on blocking based on network characteristics.

Choosing Between WAF and Network Firewall
The choice between deploying a WAF, a Network Firewall, or both, depends on the specific security needs and the nature of the digital assets an organization seeks to protect. Here are some guidelines to consider:
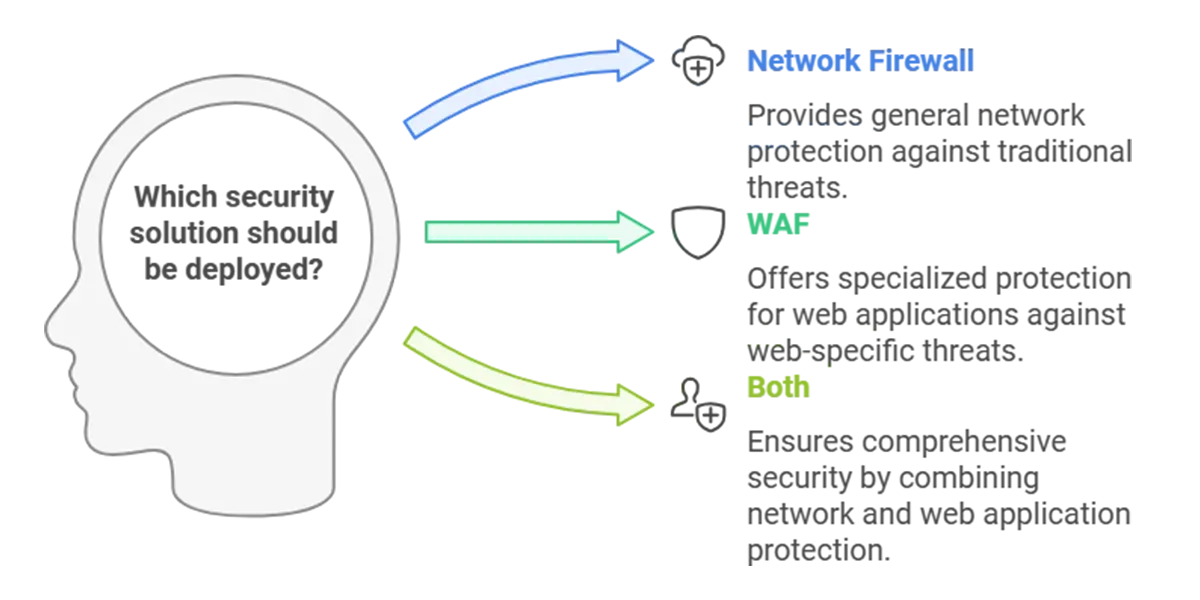
- For General Network Protection: Organizations with a broad range of network services (e.g., file sharing, remote access) should implement a Network Firewall as a foundational element of their network security strategy. This will help protect against traditional network threats and unauthorized access.
- For Web Application Protection: If an organization hosts web applications that are accessible over the internet, deploying a WAF is crucial. This will provide specialized protection against web-specific threats, ensuring the integrity and availability of web applications.
- For Comprehensive Security: Many organizations a layered security approach, employing both WAFs and Network Firewalls. This combination provides comprehensive protection against both network-level and application-level threats, ensuring a robust security posture.

Conclusion
In conclusion, while both WAFs and Network Firewalls are essential components of an organization’s cybersecurity arsenal, they serve distinct purposes and offer different levels of protection. Understanding the differences between these technologies is critical for constructing an effective security strategy. By knowing when to deploy a Network Firewall, a WAF, or both, organizations can enhance their security posture, protect their digital assets from a wide range of threats, and maintain the trust and confidence of their customers and stakeholders in the digital age.
As the threat landscape continues to evolve, the importance of making informed decisions about security infrastructure will only grow, underscoring the need for a thorough understanding of WAF vs Network Firewall and the roles and capabilities of both, to ensure a robust and comprehensive security solution.